help.sitevision.se always refers to the latest version of Sitevision
Add module
The modules use the information that the filters supply to perform the login.
Developers can create their own modules and use them in SiteVision. Further information about this can be found on page Custom JAAS modules (only available in English)
Client address
The module uses the information that the Client address filter picked from the client to save as identification for the user
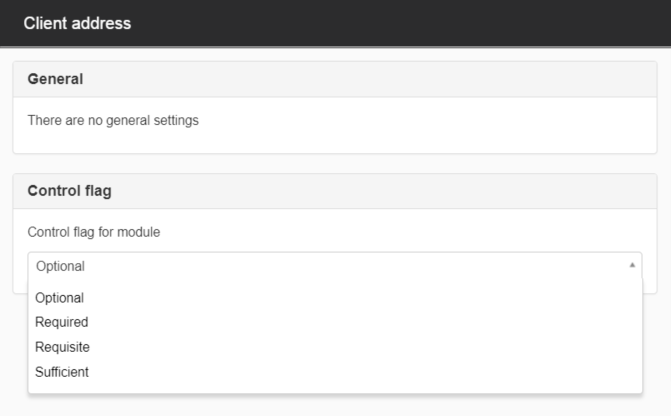
Control flag for the module -
- Optional
- Required
- Requisite
- Sufficient
LDAP
The LDAP module uses the directory service that is set up for the current website to verify the username and password.
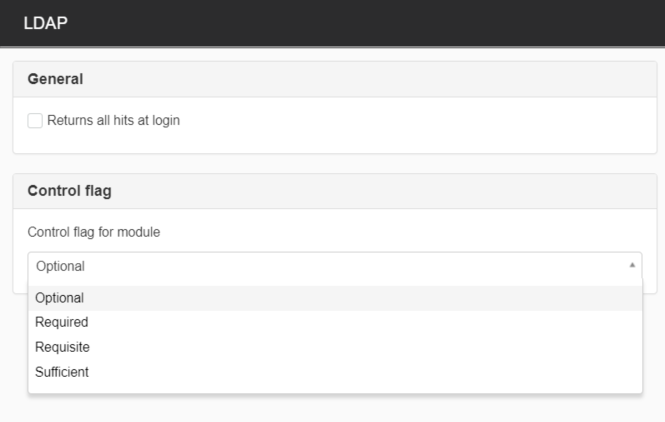
- View all login results - Used if you have users with the same username in multiple directories, this allows the user to be given the option to choose which user to use when logging in.
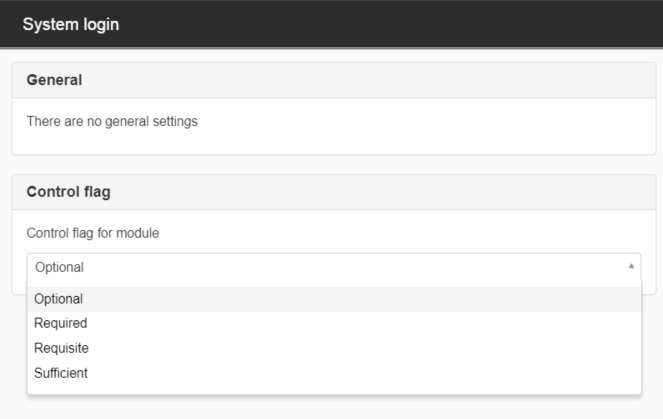
System login
This module is used to verify the login of the system user.
The control flag should be sufficient.
Secure cookie
This function enables you to enable automatic login for users. The user can choose to save their login so that the session is stored in a secure cookie.
The module requires a secure connection, learn how to enable it.
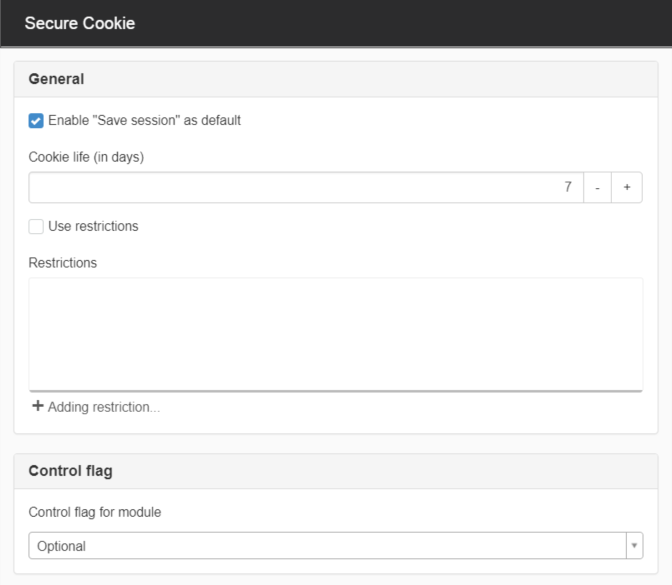
- Set "Save login" by default -Select if login should be saved by default.
- Cookie lifetime (number of days) - The validity period expires if the user does not visit the website within the selected number of days and must log in again.
- Use restrictions - Conditions to restrict the option to save logins based on criteria.
Click Add restriction to add a restriction. - Control flag - must be Optional.
Social Authentication
SAML 2
SAML stands for Security Assertion Markup Language and is an XML-based open standard for exchanging authentications and permissions.
SAML is a federated login method that organises your own login against AD without the need for direct contact with AD.
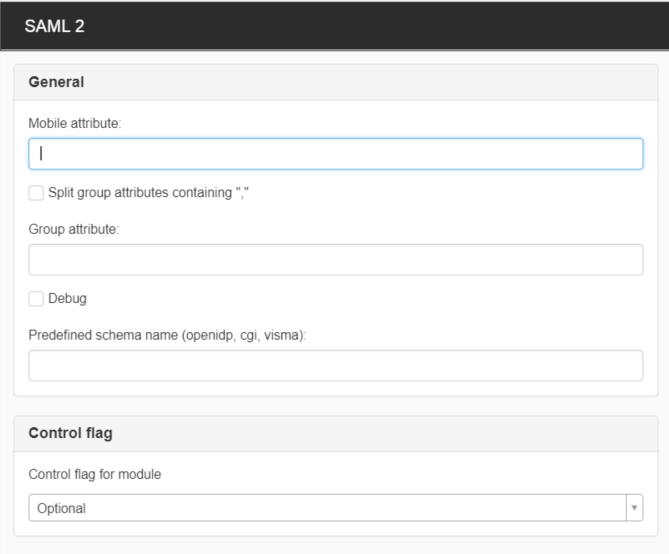
- Mobile attribute - To read in attributes for mobile numbers.
- Split group attributes containing "," - When you have a composite group attribute where the groups are separated by commas. Normally, the attributes have separate attribute values and you thus do not need to check this box. If you check the box and the attributes are not combined, the SAML configuration will not work.
- Group attributes - This attribute is used by SiteVision to set up virtual groups to manage permissions. This can be a name or a search path in the directory. <saml:Attribute Name = "the name of the group attribute". > These attribute values are those that are set up as virtual groups.
By using the Firefox add-on "SAML Tracer", you can get help to find the names of these group attributes.
- Debug - Prints detailed information in SiteVision’s server log. Good to turn on when setting up. But turn off this box when SAML is in production (generates many log printouts).
- Predefined attribute schedule (openid, cgi, visma) - Print the predefined schedule that you want your setting to follow.
- Control flag - Should be Sufficient.
SAML should precede LDAP in the list of login modules. If the SAML login does not work, you will be forwarded to a regular form login.
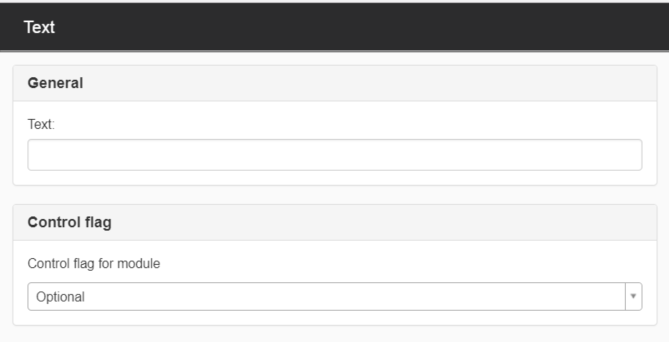
Text
This module can be used if you want text entered into the login form.
MobilityGuard
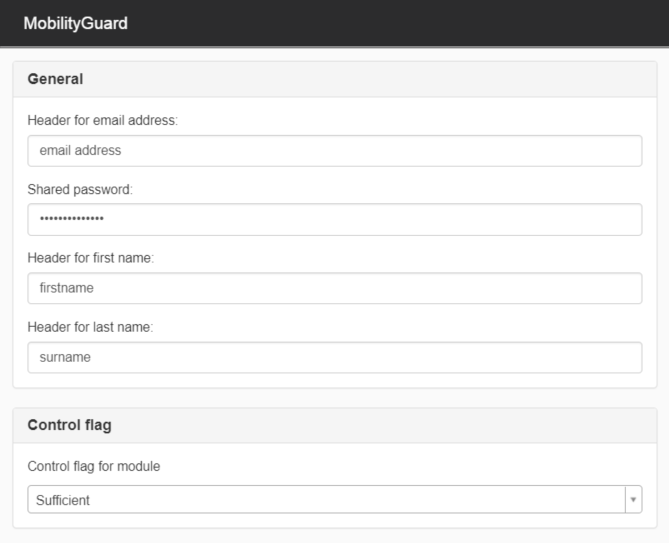
The module uses headers from the external security solution MobilityGuard External link, opens in new window. to identify users.
External link, opens in new window. to identify users.
If Mobilityguard and SiteVision are connected to the same LDAP server, the Mobilityguard filter is sufficient, otherwise you will need to use this module.
The Mobilityguard module must be after the System login module but before the LDAP module in the module configuration. System login and MobilityGuard control flag should be set to Sufficient.
Below is an image of the settings you need to make in the module. MobilityGuard sends the necessary information via headers to SiteVision. You must enter the name of the headers that come from MobilityGuard.
CAS
CAS is open source software for single sign-on (SSO) for web applications.
Instead of SiteVision managing the login, this is done by a central service outside of SiteVision.
OpenID
Module that creates the user, receives all the information from OpenID.
CAS 3
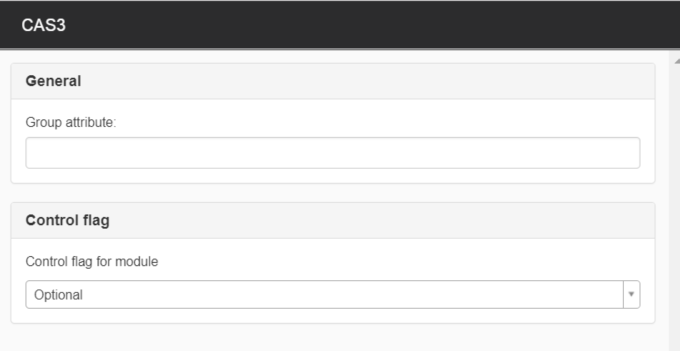
- Group attribute - Map the group attribute on the virtual group to this setting
- Control flag - Must be set to optional.
Swedish e-identity
Module that creates the user, receives all information from Swedish e-identity. External link, opens in new window.
External link, opens in new window.
The page published:

 Print page
Print page